
Slowloris is a variant of a typical Distributed Denial of Service (DDoS) attack, where attackers overwhelm targeted hosting servers. They do so to create downtime by sending, continuously, as well as maintaining numerous simultaneous and partial HTTP connections to the targeted server.
In terms of speed, it is a slow and steady attack. Yet it is quite feared because it can cause a large amount of damage in a limited time span. This post will help explain its beginnings, its functions and how it can be stopped in its tracks.
Developers of Slowloris attack
Robert Hansen aka RSnake developed it and this attack empowers individual computers to conduct large scale DDoS attacks. In comparison to other kinds of DDoS attacks, this one uses the least amount of bandwidth.
The Slowloris attack is considered to be quite effective and equally dangerous, and is quite effective even against the most well known server software too.
It is because of such a requirement that Slowloris is cost-effective and an affordable cyber-attack option for hacktivists. There have been numerous high profile server shutdowns and takedowns in all these years due to this variant, and Slowloris continues being a strong tool for hacktivism in the near future.
When did the largest Slowloris attack take place?
One of the largest Slowloris attacks and incidents of Hacktivism happened during the 2009 Presidential Election in Iran. Iranian hacktivists took down numerous government websites and disrupted state services.
How does it work?
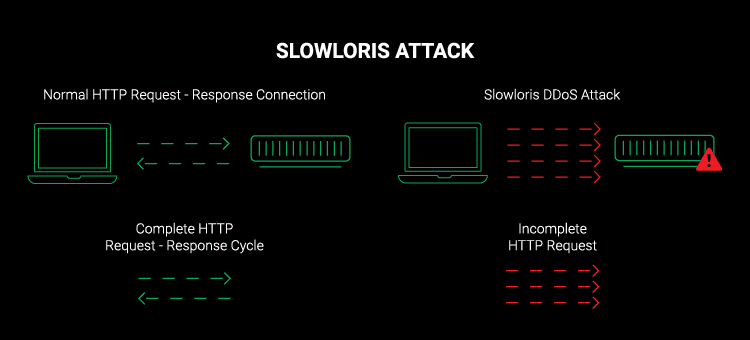
A Slowloris attack is an application layer attack of sorts. It bombards internet users with slow internet network speeds and poor connectivity, which hence hurts their connections to web apps
This attack works by opening numerous partial HTTP requests to targeted web servers. When these connections are kept open for long time periods, attackers can keep sending those requests even if they are incomplete.
On the other hand, the attacked servers keep the connection open, and they wait for each attack request to be completed. Once the maximum server limit is reached, legitimate network connection requests will hence be denied. This is how a Slowloris attack fractures a network and creates a denial of service.
Why is this attack highly effective and quite dangerous?
Slowloris DDoS software is designed for carrying out DDoS attacks in a stealthy manner. It basically plays the game of laying low and moving slow. Once it is initiated, it waits for sockets to be released by legitimate requests. When consuming them one after one, even if it is a high volume website or web app, it attacks both.
Countering a slowloris attack is possible by high-volume websites but only if they are detected, and for legitimate sessions to start again.
Unlike other kinds of DDoS attacks sending malicious content or malformed packets, A Slowloris attack sends partial HTTP requests which can slip past traditional anomaly scanners as well as detection systems.
It does not cost attackers to acquire the bandwidth to launch such an attack as it uses minimal bandwidth. Slowloris DDoS attack software basically empowers an individual computer to take down a complete high-profile server. This is why attackers using Slowloris attacks opt for Hacktivism.
Can the Slowloris software be modified?
The Slowloris software can be modified and altered easily. This helps attackers send different kinds of host headers. It also helps them store separate logs for each host provided the target is a virtual host. It is capable of silencing creation of log files during an attack.
This hence enables it to catch unmonitored web servers by surprise and go past their detection systems without creating any alarm or red flag in the log file entries.
Ways to stop the Slowloris attack
It is possible to prevent Slowloris attacks in vulnerable web servers to prevent further layer 7 DDoS attacks through the following measures:
- Limiting incoming requests based on usage factors. This helps access to vulnerable web servers to become restricted on factors like maximum duration, number of connections allowed from an individual IP address, transfer speeds and vice versa.
- Hiring a DDoS proxy protection services can put the business in a good place through implementation of a comprehensive cybersecurity plan and security measures. These can gho beyond the conventional measures and provide holistic security solutions against most cyber attacks, and especially Slowloris DDoS Attack.
Conclusion
Comprehensive solutions that can easily detect all sorts of anomalies can be considered as DDoS protection software which is worth the investment. Such solutions must have cutting-edge technology which combines both human expertise and top notch intelligent solutions to help counter both the Slowloris DDoS attack and other forms of DDoS attacks.
Such solutions should have the surgical accuracy which should be inline with the needs and risk profiles of the business using these solutions.
Moreover, such a solution should be able to monitor websites and web applications round the clock for detecting any suspicious activity plus any anomalies in the web traffic. It should also be able to send real-time alerts and insights to ensure such attacks are stopped in their tracks, and website/web-apps are available 24/7.




![How to Fix [pii email 9ba94c086590853d8247] error code in Microsoft Outlook 8 [pii email 9ba94c086590853d8247] error code in Microsoft Outlook](/media/2021/10/pii-email-9ba94c086590853d8247-error-code-in-Microsoft-Outlook-390x220.png)